VCF 9 – CA Integrated Certificates Management
In production environments, it is assumed that certificates need to be replaced; however, this is equally important and applicable to labs and staging environments as well. From my experience, establishing a communication-healthy trust relationship with all components that integrate will result in fewer headaches and most likely fewer clicks. Honestly, this is the first thing I look for after deploying a new solution, especially if it will integrate with other solutions.
A word of advice:
- Having self-signed certificates is just not right.
- Create a private CA, you know it’s right.
- Replace those certificates, even if it’s not light.
- Your browser will be happy for many days and nights.
In VMware Cloud Foundation 9, managing certificates is done via Fleet Management within VCF Operations. However, there are a couple of things to highlight based on the new architecture:
- VCF Management (Fleet Management, VCF Automation, and VCF Operations) features a dedicated certificate management integration, which can only be integrated with Microsoft CA (currently).
- VCF Instances (SDDC Manager, NSX Manager(s), vCenter AND ESXi Hosts) have a dedicated certificate management integration, which can be integrated with both Microsoft CA and OpenSSL (similar to what was previously available in previous VCF versions).
- There is a new feature that allows you to toggle the automatic renewal of certificates. Now, technically speaking, this is highly beneficial in case something slips the radar. Operationally speaking, maintenance windows are not going away, and that single user who never used any of the portals will raise a ticket because the portal was not accessible at the time to test their login. But what do I know about maintenance windows?
In this blog post, the integration will be Microsoft CA-based, as in my lab, I have Active Directory Domain Services (ADDS), DNS, Certificate Authority (CA), and Network Time Protocol (NTP) services all integrated into the domain.
Prerequisites:
- A Microsoft CA Server with its respective roles enabled and configured.
- A published certificate template dedicated to the VCF.
The steps apply to both VCF Management and VCF Instances:
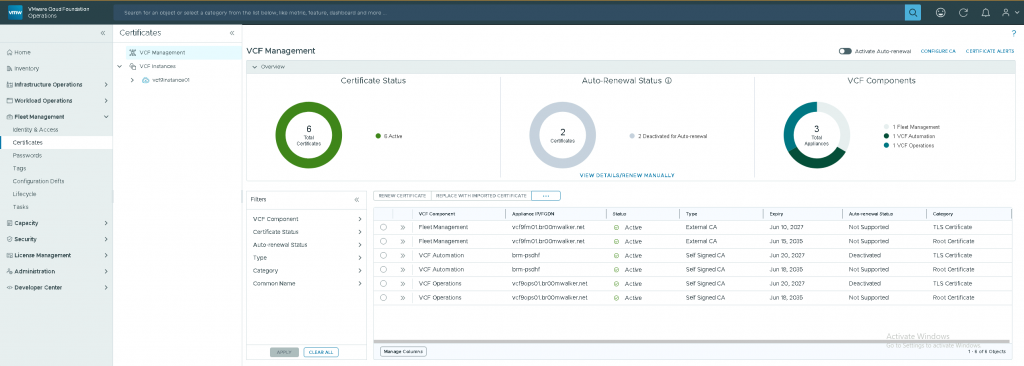
- Click on “CONFIGURE CA“:
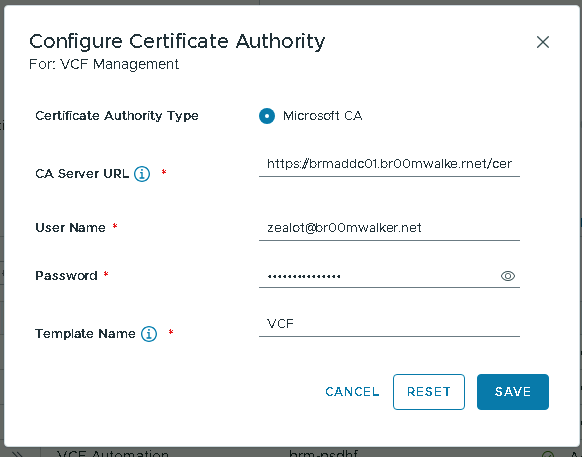
- Microsoft CA Configuration parameters:
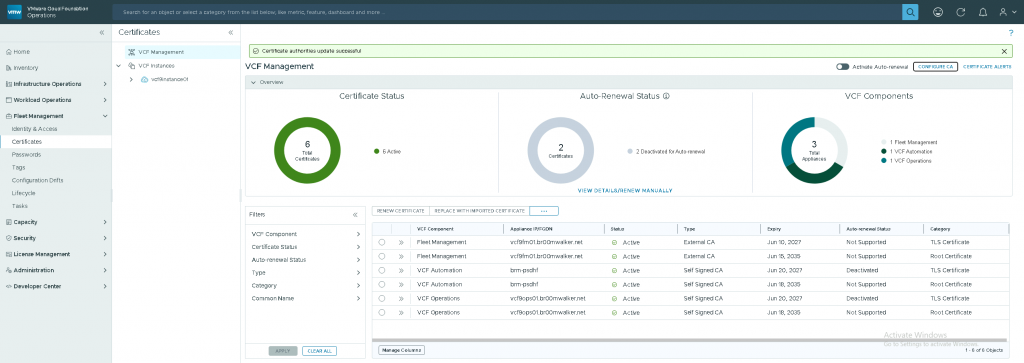
- CA Configuration Updated Successfully:
- Select any VCF Component where the category is “TLS Certificate” and not “Root Certificate“, as the Root will be updated to the Microsoft CA Root once the certificates are replaced.
- Click on the three dots “…“.
- Generate the CSR.
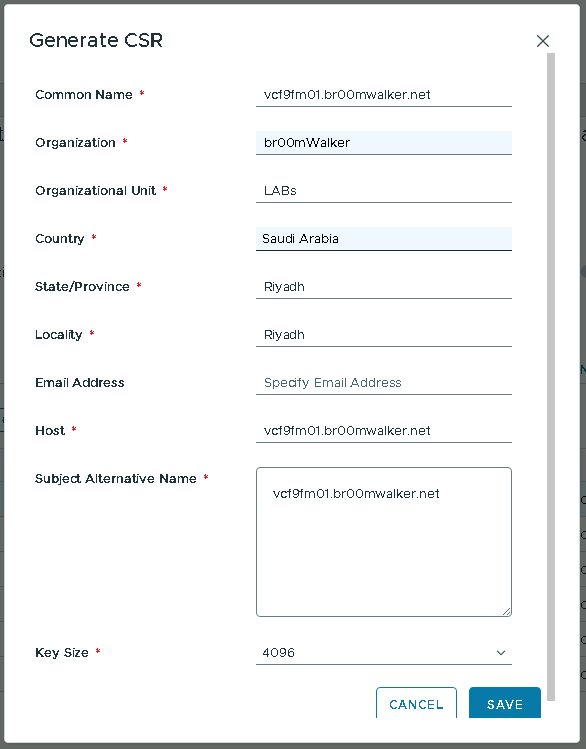
- Populate the certificate request details and SAVE:
- Click on the three dots again “…“.
- Choose “Replace with Configured CA Certificate” and Confirm.
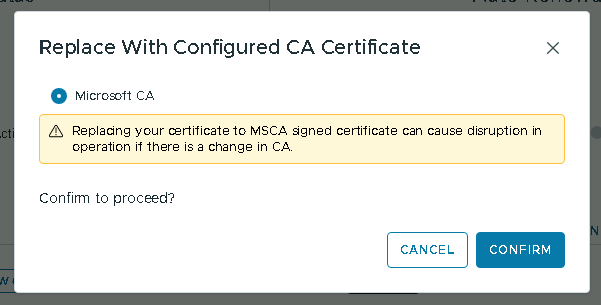
- The process takes a couple of minutes to complete.
- You can run one replacement request at a time, although it is clickable, and by god, I did click it! It was not appreciated and it utterly failed :).
- The process finishes at the component level much faster than its reflection in the “VCF Operations” UI, so you will have to give it a couple of additional minutes for the UI to reflect. However, once the task is completed, you can directly go to the component to check and verify.
- Then you can iterate across the different VCF components within VCF Management and VCF Instances.
- VCF Management:
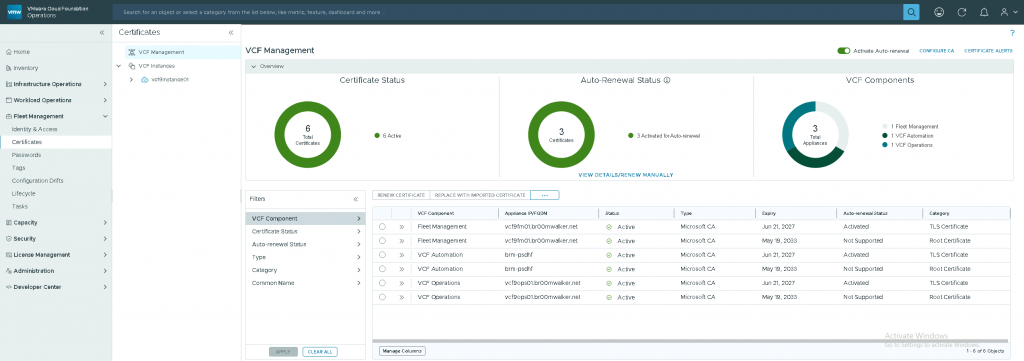
- VCF Instances:
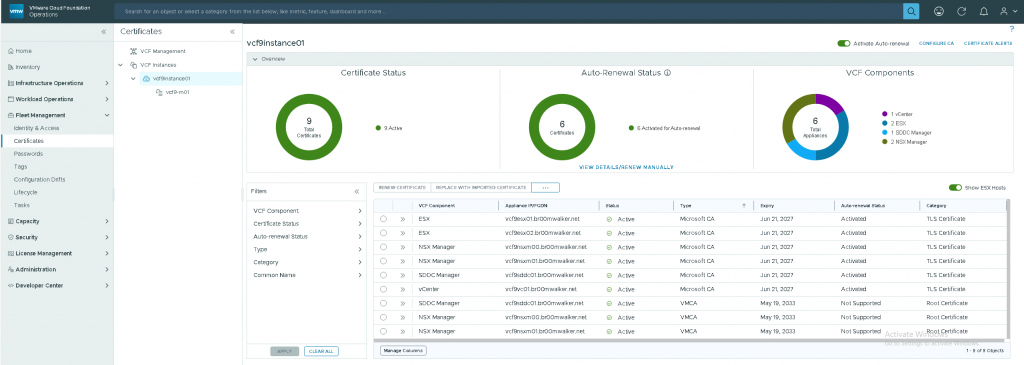
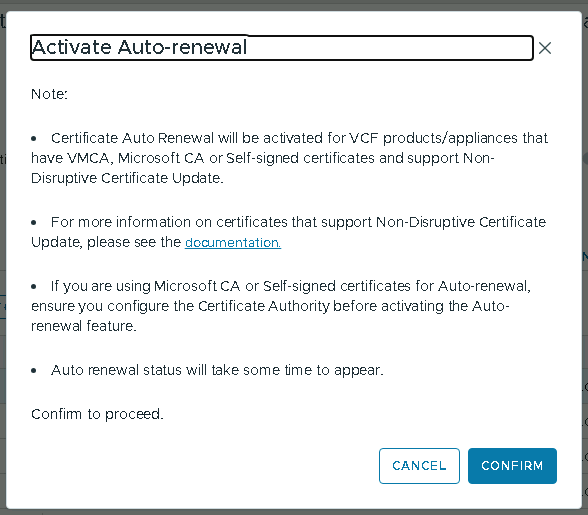
- Optionally, you toggle the “Activate Auto-renewal” option for both VCF Management and VCF Instance.
- It will take a couple of minutes for this option to populate in the UI (I’ll let you know how it went in a year or so %)).
- Don’t upset your CA server if this gets enabled ;-).