Eyeing The Credentials: Mitigating The Leak
I’ve been in the IT business for around 20 years now, and I’ve seen my good and fair share of IT related dilemmas, one of the most pressing ones in our days is maintaining a “leakage free” credential environment.
Whether you’re willing to admit it or not, most of the users whether being on the internal network or external network, being employees or customers, there is always a certain amount of self-security-commitment that one can enforce oneself. Not that because its hard, nor being it requires a lot of effort, but in the middle of the business chaos and while looking to cater for the business objectives and achieving the business goals, security awareness slips into the routine.
In the past couple of years you’ve most probably noticed the high-rise of data leak, whether its email addresses, credentials, customer databases, a lot of information can be useful to someone these days to most likely inflict harm and create a massive headache for CxOs in any corporate.
Its obvious that this level of awareness needs to be nurtured and addressed with proper security-based-enablement. However what is much more important at this point in time is have the ability to lock down leaks, mitigate the risk of leakage and remediate the gaps and root causes.
As you would have imagined by now, doing this at scale, no matter the size of the IT operations, this will be a tremendous amount of manual work and most likely will not be as fruitful as it is anticipated, also keep in mind that having multiple tools to get into a means would be also a challenge from an integration perspective.
Now that we have pin-pointed the problem, lets go through an interesting solution that I believe would have a huge impact on any corporate security operations, IntSights.
IntSights has a suite of products and solutions that addresses the topic of threat intelligence particularly as they’d like to call this endeavor “Eliminate the Complexity of External Threat Intelligence“. To get you up to speed Vladan SEGET wrote an introductory blog on External threat protection and cybersecurity intelligence | ESX Virtualization (vladan.fr), also Mike Letschin detailed some of IntSight’s TIP (Threat Intelligence Platform) Time to get back in the driver’s seat of security | | The Solutions Architect.
From a process perspective IntSight’s TIP follows a methodology to get the corporate into its desired security posture from a data leakage mitigation perspective.
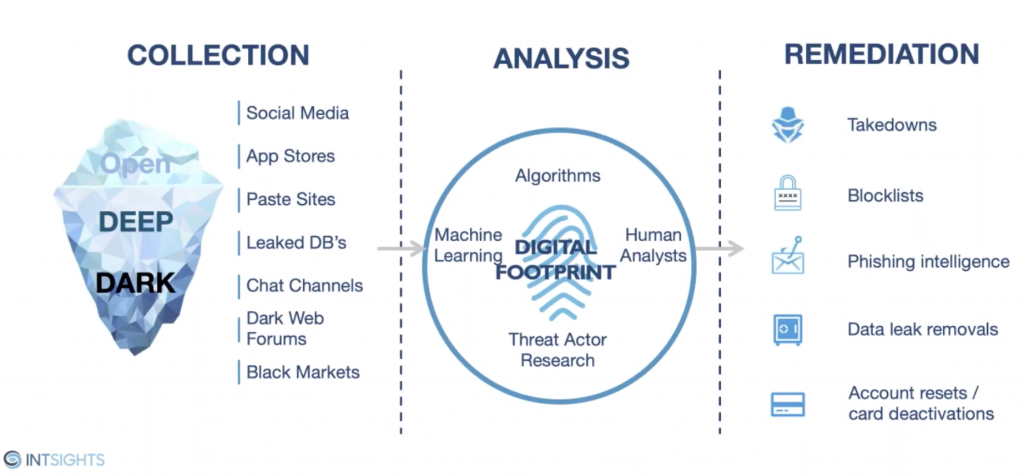
And all of this is done in an automated fashion, and this is ideal to address the pace of the attack vectors that exists in our times, and most likely this is going to evolve in the near and far future.
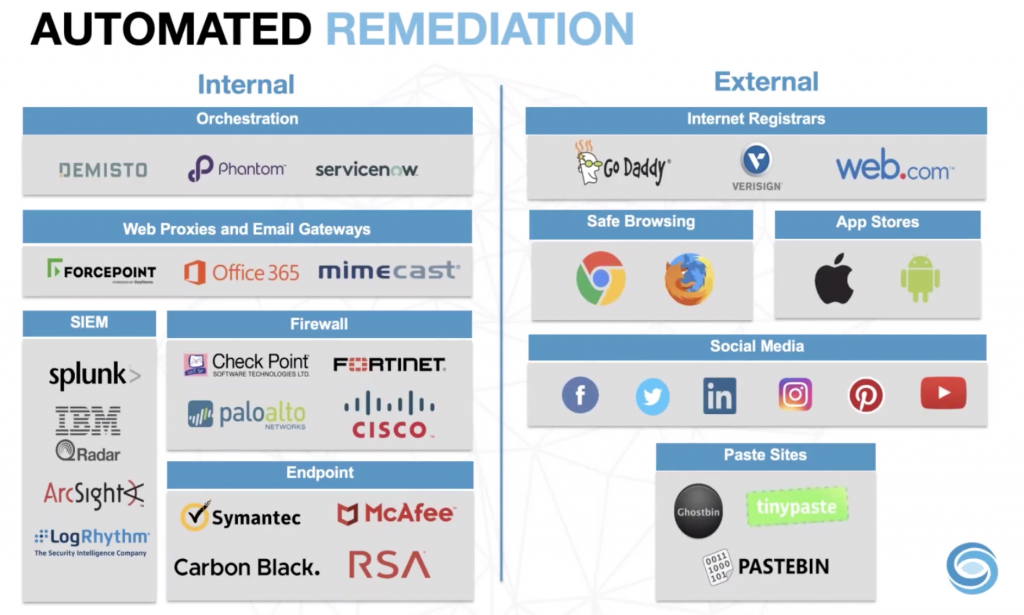
Having the correct tooling that is capable of integrating with your different platforms and leveraging that tooling’s capability will ultimately work for the best interest of your security operations and will most likely be of a huge added value when something massive is unleashed against the internet in its entirety.
When thinking about being security-ready, having a tool that integrates and provides you with not only analysis but mitigation is key to the sustainability of any corporates face.
I’d recommend going through IntSights different resources, especially the webinars, and if you like what you see (which you will), request a demo and engage with IntSight’s team to see how they can help you move from the “oh, what should I do” vector to the “BRING IT ON” vector ;-).
Note: this is a sponsored post, my first one too ;-).